DRILL RAT is being used to accomplish remote access and persistence on the victims. The payload, delivered as a compiled executable, is not detected by the Windows Antivirus (Defender). Besides that, the compiled payload has Anti-VM/Sandbox capabilities.
Our researchers were in contact with the actor “serser23l” through the XSS hacking forum and obtained additional information about the advertised RAT.
The actor was active on the Telegram chat application where they used the handle Artemis and the username @lulske1.
A payload could be generated using the DRILL v1.0 panel which would be provided to a buyer upon a successful transfer of funds. The actor revealed they are using the following Bitcoin wallet address: 36dkHmSwaUUTrv8YoDEERafFNqBnpAjz1J
Based on the information provided by the actor, the panel could generate payloads for both the Windows and Linux operating systems.
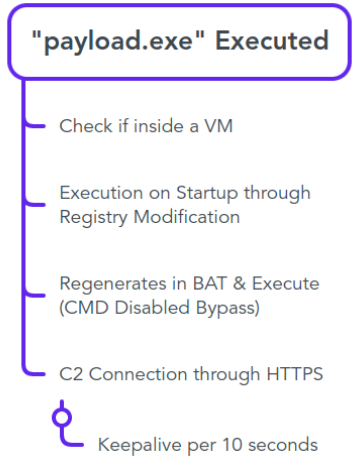
The final generated payload was provided to our researchers as a compiled executable named “payload.exe”.
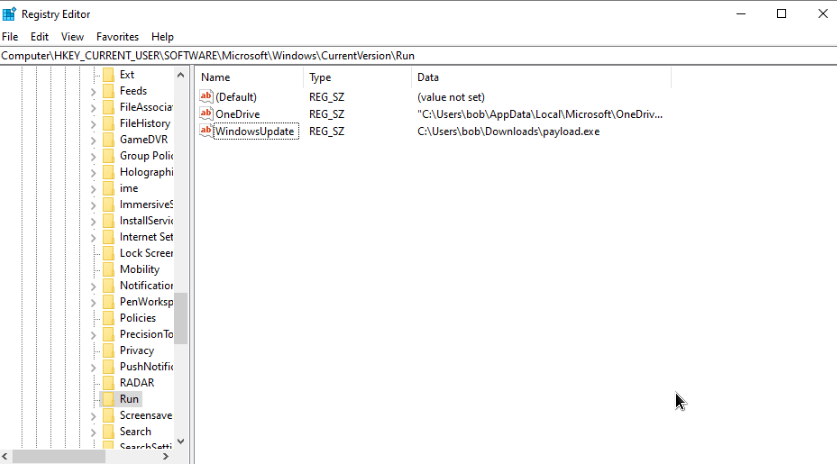
Once executed, the payload adds itself in AutoRun through registry:
- Registry Location: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Key Name: WindowsUpdate
- Key Value: DRILL Implant executable’s full path
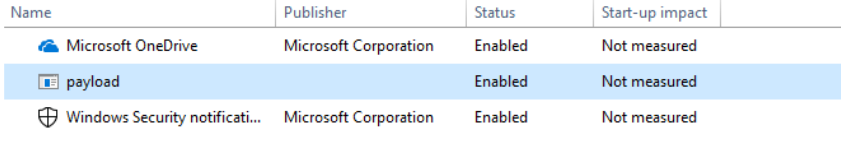
We can confirm its way of persistence by analyzing the Startup processes.
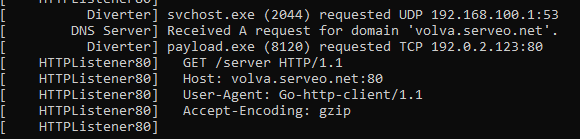
After that, it tries reaching a hostname (volva.serveo.net), which appears to be a proxy service for internal IP addresses.
The keepalive is being sent each 10 seconds.
During our static analysis, we discovered that the C2 endpoint is hardcoded within the executable:
Also, besides that, we identified a unique path that was used during the build of the executable:
This would allow us to create an effective YARA rule to detect the implant in the wild.